Let’s discuss the question: how can rainbow tables be defeated. We summarize all relevant answers in section Q&A of website Myyachtguardian.com in category: Blog MMO. See more related questions in the comments below.
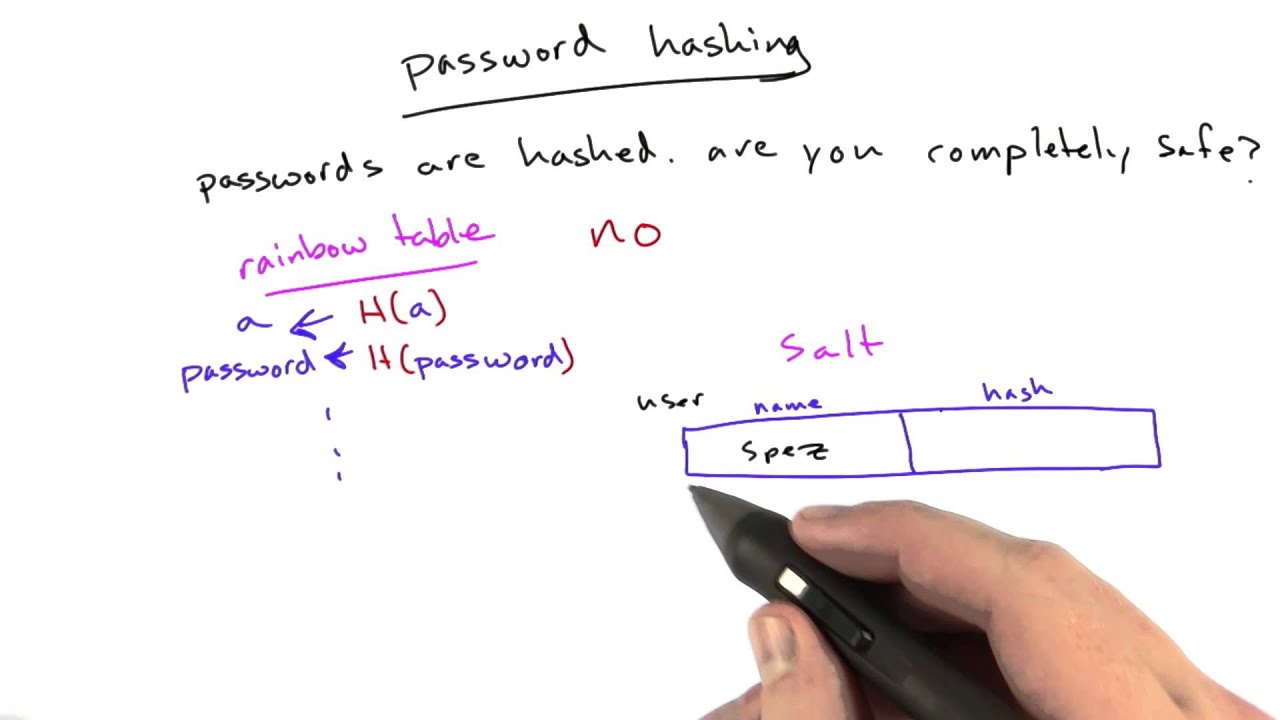
Table of Contents
How are rainbow tables defeated?
The prevalence of rainbow table attacks has dramatically decreased due to a technique known as “salting.” Salting is a modern technique used to thwart rainbow table attacks. It involves adding an extra random value to every hashed password to create a different hash value.
What is the Defence for rainbow tables attacks?
Experts say the best defense against rainbow tables is to “salt” passwords, which is the practice of appending a random value to the password before it is encrypted.
Rainbow Tables – Web Development
Images related to the topicRainbow Tables – Web Development

Are rainbow tables effective?
Rainbow tables greatly speed up many types of password cracking attacks, often taking minutes to crack where other methods may take much longer (e.g., dictionary, hybrid, and brute-force password cracking attempts).
What are the advantages and disadvantages of rainbow tables?
- Hacker attacks using Rainbow Tables have the advantage of most data being pre-computed, resulting in an easy hack access. …
- Another crucial advantage using of Rainbow Tables is the ability of authentication without serious obstacles.
What is the purpose of rainbow tables and what is the best defense against them?
Rainbow tables have evolved along with enterprise security; here’s how to protect against them. Rainbow tables allow an attacker to crack passwords far more quickly than is possible using other methods, such as brute force attacks.
What is Salting a password?
A salt is a piece of random data added to a password before it is hashed and stored. Adding a salt to stored passwords is a security process used alongside the hashing of passwords before they are stored.
How does password salt prevent rainbow attacks?
A salt randomizes each hash by adding random data that is unique to each user to their password hash, so even the same password has a unique hash. If someone tried to compare hashes in a rainbow table to those in a database, none of the hashes would match, even if the passwords were the same.
Does salting prevent rainbow tables?
Additional Measures. While a salt effectively prevents the use of a rainbow table, it does not make it in any way more difficult to attack a single password hash.
What is password spraying?
Password spraying is a type of brute force attack. In this attack, an attacker will brute force logins based on list of usernames with default passwords on the application.
How do rainbow table attacks work?
What Does Rainbow Table Attack Mean? A rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored in a database system. A rainbow table is a hash function used in cryptography for storing important data such as passwords in a database.
What is the difference between rainbow table attacks and dictionary attacks?
The difference between Rainbow Tables and other dictionaries is simply in the method how the entries are stored. The Rainbow table is optimized for hashes and passwords, and thus achieves great space optimization while still maintaining good look-up speed. But in essence, it’s just a dictionary.
Which of the following would provide the best protection against rainbow table attacks?
Salt is added to a password to prevent rainbow table attacks.
Password Cracking 201: Rainbow Tables
Images related to the topicPassword Cracking 201: Rainbow Tables

What are the three advantages of a rainbow table over other password attacks?
Three advantages of a rainbow table are: (i) A rainbow table can be used repeatedly for attacks on other passwords. (ii) Rainbow tables are much faster than dictionary attacks. List and describe three of the common password setting objects.
How does Rainbow Crack work?
RainbowCrack is a computer program which generates rainbow tables to be used in password cracking. RainbowCrack differs from “conventional” brute force crackers in that it uses large pre-computed tables called rainbow tables to reduce the length of time needed to crack a password drastically.
Why is it called a rainbow table?
The reason they’re called Rainbow Tables is because each column uses a different reduction function. If each reduction function was a different color, and you have starting plaintexts at the top and final hashes at the bottom, it would look like a rainbow (a very vertically long and thin one).
What is hash password?
When a password has been “hashed” it means it has been turned into a scrambled representation of itself. A user’s password is taken and – using a key known to the site – the hash value is derived from the combination of both the password and the key, using a set algorithm.
Why do we salt password?
Even when the same input is used, it is possible to obtain different and unique hashes. These hashes aim to strengthen security, protect against dictionary attacks, brute-force attacks, and several others. Most commonly, salting is used in common passwords to strengthen them.
What are rainbow attacks?
A rainbow table attack is a hacking method that involves the use of a rainbow hash table. This table contains the values used to encrypt the passwords before adding them to the database.
Can you Unhash a password?
No, they cannot be decrypted. These functions are not reversible. There is no deterministic algorithm that evaluates the original value for the specific hash. However, if you use a cryptographically secure hash password hashing then you can may still find out what the original value was.
What is bcrypt password?
Rounds. variable via cost parameter. bcrypt is a password-hashing function designed by Niels Provos and David Mazières, based on the Blowfish cipher and presented at USENIX in 1999.
How does password hash work?
Hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, cyber criminals don’t get access to your password. Instead, they just get access to the encrypted “hash” created by your password.
What does salting passwords prevent?
Password salting is a technique to protect passwords stored in databases by adding a string of 32 or more characters and then hashing them. Salting prevents hackers who breach an enterprise environment from reverse-engineering passwords and stealing them from the database.
Generating Rainbow Tables With RainbowCrack
Images related to the topicGenerating Rainbow Tables With RainbowCrack

What attacks can salting prevent?
Salting your passwords helps prevent attacks, such as hash table attacks, by forcing hackers to re-compute the hash values and using the salts for each user. A cryptographic salt is made using random bits added to every password instance before hashing it, making your password strong and secure.
How can hash collision be prevented?
The best way to avoid collision is to use a good hash function that distributes elements uniformly over the hash table. There also various collision resolution techniques like open hashing, closed hashing, double hashing, etc. Hash table is a data structure that uses a hash function to map elements(keys) to an index.
Related searches
- an nmap scan of a server shows port 25 is open. what risk could this pose?
- does kd matter in rainbow six siege ranked
- rainbow 6 siege can’t reconnect to ranked
- john the ripper is a technical assessment tool used to test the weakness of which of the following?
- are rainbow siege servers down
- what statement is true regarding lan manager lm hashes
- rainbow 6 siege can’t find game
- rainbow 6 siege single player review
- john the ripper is a technical assessment tool used to test the weakness of which of the following
- does kd matter in r6
- infosec skills
- rainbow six siege kd reset
- rainbow siege tips
- cannot connect to rainbow six siege servers
- an nmap scan of a server shows port 25 is open what risk could this pose
- skillset labs
Information related to the topic how can rainbow tables be defeated
Here are the search results of the thread how can rainbow tables be defeated from Bing. You can read more if you want.
You have just come across an article on the topic how can rainbow tables be defeated. If you found this article useful, please share it. Thank you very much.

